Information Technology Updates
College of Education recently completed a new series of lunch and learn presentations by faculty, called “Big Ideas Small Bytes”. Six presentations were organized by their Educational Technologist, Farah Kashef, and delivered by the faculty, and one graduate student, from various areas of the college. The focus of the series was to share experiences on newly adopted pedagogical approaches that lead to more student engagement and learning _ Big Ideas. There was usually a technology piece that was tied in the experience being presented _hence, “Small Bytes”; pun intended? Maybe! For the TPACK fans, this was more focused on the TPK segment of the concept.


Although the presentations were in an informal environment (most were in the faculty lounge area of the Schindler Education Center), all were exceptionally of high quality, meaningful, and thought-provoking where student learning was first and technology second. College of Education will continue to have the Big Ideas Small Bytes series in the upcoming fall semester. The spring presentations were:
1- Beginning with the end in mind... utilizing technology as a tool; by Dr. Kim Huckstadt
2- Guiding Students to High-Quality Resources: Rod Library research Guides; by Anne Marie Gruber and Katelyn Browne
3- Using free and open-source game development platform, ARIS, to enhance lessons; by Dr. Dana Atwood-Blaine
4- Making professors' implicit expectations explicit to their students through more transparent assignments: A micro-workshop; by Drs. Elana Joram, Shuaib Meacham, and Susan Hill
5- A Techno-Illiterate Septuagenarian's Use of Media Tools; by Dr. Tom Davis
6- Steven’s Journey: The Evolution of Technology for Guiding a Career Path; by Steven Blair –Graduate student.

Over the coming months, Information Technology will be rolling out an additional feature for the campus notification system called Alertus. Alertus is a desktop notification client that works in concert with the UNI Alert system. When a UNI Alert is issued, those issuing the alert have the option to include Alertus as a notification step. This will send a full-screen pop up informational window to desktop and laptop computers that have the Alertus notification client installed. The client will be installed for digital signage computers, classrooms, computer labs, and will be available for your office computer as well. The following schedule gives an approximation of when the Alertus client will be rolled out where:
- Alertus will be installed for all digital signage by April 13th
- Alertus will be available for you to install on your office desktop or laptop via Software Center (Windows) or Self Service (Mac) by April 13th
- Alertus will be installed for classroom computers after the Spring 2018 semester has come to a close - the week of May 7th
For more information on the Alertus Notification Client, please see the following website: https://it.uni.edu/services/alertus-notification-client
If you have questions, comments, or concerns, please contact Information Technology Service Desk at 273-5555 or via email at servicedesk@uni.edu.
By Leigh Zeitz and Magda Galloway
Instructional Technology, Curriculum and Instruction, College of Education.
The 20th century idea of a computer lab involved rows of desks containing rows of computers with monitors on top. The computer teacher stood in the front of the room and the students peered around the monitors to see what computer teacher was sharing on her screen.
When Schindler Education Center was remodeled, we decided to rethink the essence of a computer lab. The concept of computing has changed. For the past decade, laptops have outsold desktops. A UNI survey found that 97% of our undergraduate students own laptops. What sense does it make to provide computers for students when they are more comfortable using their own?
So we created Room 133, a computer lab without desktop computers. Notice that we didn’t say “without computers” because we also have carts containing MacBooks, Chromebooks, and iPads . These computers are available for students who don’t have computers or their laptops are on the fritz. They are also quite useful when we want to engage our students in brand-specific software or we want to provide our students with the Chromebook or iPad experiences that they will probably have in their schools. Room 133 uses the baseline classroom configuration used across campus so teachers and students new to the environment can find familiar resources.
Room 133 includes non-computer resources as well. Our laptop cases store playful hands-on manipulatives (e.g., OSMOS; Dash and Dot Robots; and Bloxels.) It’s close proximity to the IRTS library in Schindler allows us to bring exciting enrichment tools like their Google Expedition cart to engage students in augmented-reality learning.
So what makes it a computer lab if it is not filled with computers? It is the infrastructure that supports computer-based learning. We have provided a flexible learning space. Our students have their choice of seating arrangements and choice of computer platforms. Integrating G Suite for Education into our curriculum provides us with a virtual collaborative space in the Google Cloud.
Technology’s place in the classroom fulfills the need for the right tools to support class projects. We structure the bulk of our assignments around collaboration, interactivity and striving towards using technology to redefine the learning process. Providing our students with the tools and opportunities to make decisions in their learning creates a student-centered learning environment. This process of modification or redefinition of the learning tasks is something that is advocated in Iowa’s schools using the SAMR model. We also integrate technology into the learning process using TPACK model where Technology finds a place to support Pedagogy and the Content Knowledge.
Another aspect of Room 133 is the mobile furniture that we have available. Desks and chairs are on wheels and various types of mobile furniture provide choice for our students. The advantage of our mobile furniture is that we can freely arrange the desks and seats as needed for teamwork. This flexibility is supported by the portable white boards and dry erase markers that are available for each student.
Room 133 is not a finished project. We like to consider it an ongoing enterprise where we are exploring new ways to provide unique learning opportunities for our future teachers. These experiences will expand their learning now and model possibilities that they can use with their students in the future.
Information Technology has scheduled a planned maintenance outage to install important security patches for the campus Student Information System. Outage details are below.
Scheduled For:
Sunday, March 4th from 7:00AM to 3:00PM
Applying Operating System patches, Campus Solutions Bundles, and Crystal Report Server PeopleTools patches.
Impacted University Services:
- Student Information Systems
- Peoplesoft Campus Solutions
- Student Center
- Advisor Center
- Faculty Center
- My Universe Portal
- Peoplesoft CRM Systems
- Online Application for Admission
- Online Course Lookup
The following will only be impacted for the first hour:
- My Universe Portal
- Peoplesoft CRM Systems
- Online Application for Admission
This outage is needed to apply application security patches to SIS Services
Contact:
UNI IT Service Desk
servicedesk@uni.edu
319-273-5555

Submitted by Jim O’Loughlin, Languages & Literatures
I’d like to say that this insight was the result of careful study and analysis, but it was something I stumbled into, like many of the best ideas.
In most of my literature and writing classes, students engage in group work, combining forces to answer a question or interpret a passage and then reporting back to the class as a whole. Such exercises typically require little technology beyond a slip of paper and maybe a chalkboard. However, often it is beneficial for groups to have a lasting record of their responses, and other times I would like students to have access to the internet as part of their collaborative efforts.
At such moments, the standard classroom with its single instructional computer doesn’t work well, but it doesn’t make sense to relocate to a computer lab for a single exercise either. I have tried setting up a word processing page or a PowerPoint file to record information. The problem that created was that the instructor computer became a bottleneck, as students had to wait for each group to write their response on the same machine. It wasn’t a good use of class time, and after one such experience a student pointed out to me that it would be possible to have multiple people edit a Google Slides file at the same time. And then it all started to come together. Since the Google App suite is already built into the UNI Gmail-based system , it is extremely easy to use.
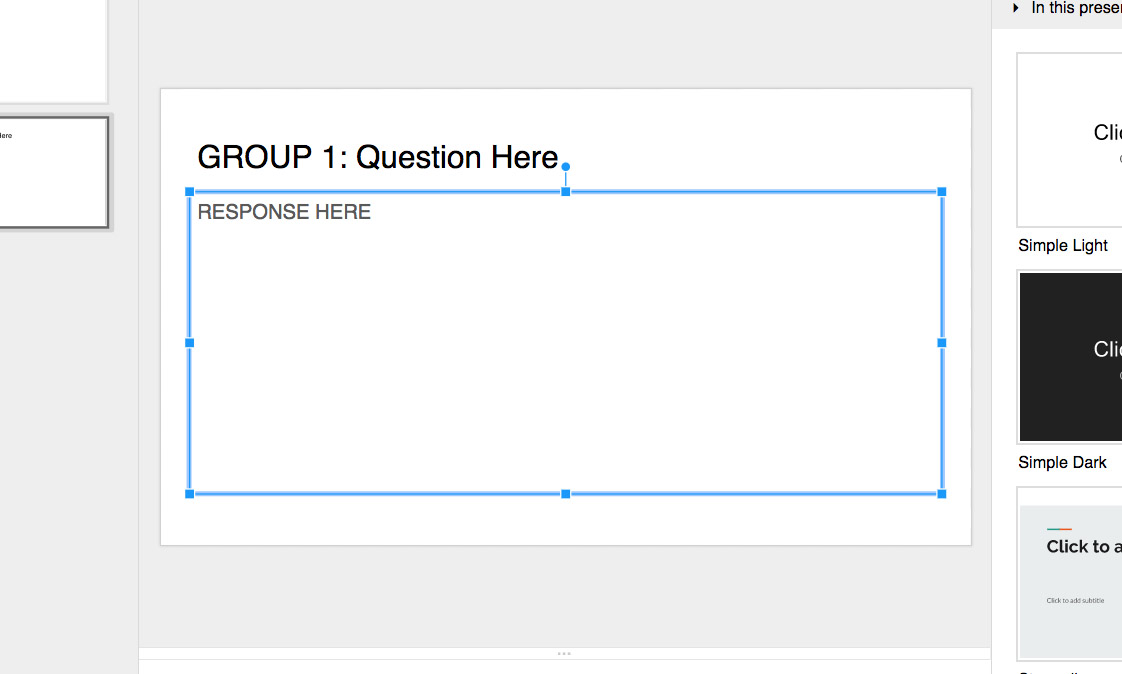
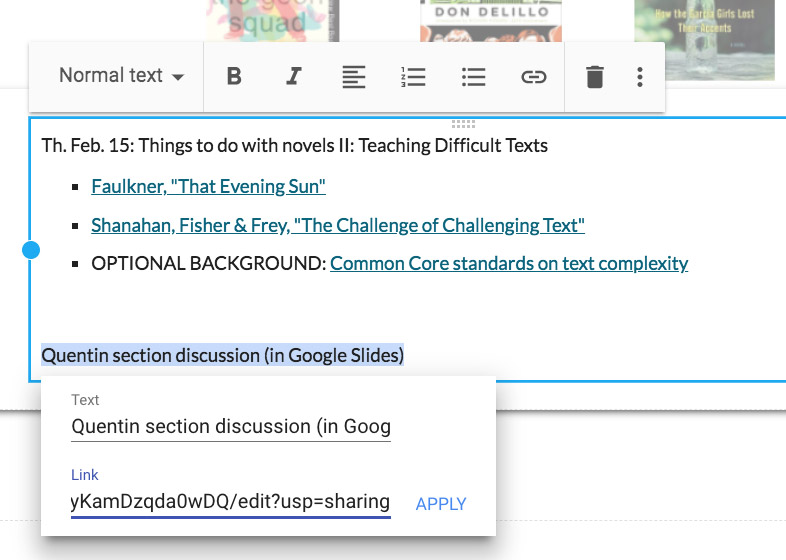
Now, before a class with group discussions, I create a Google Slides file and put a different group question or task on each slide.
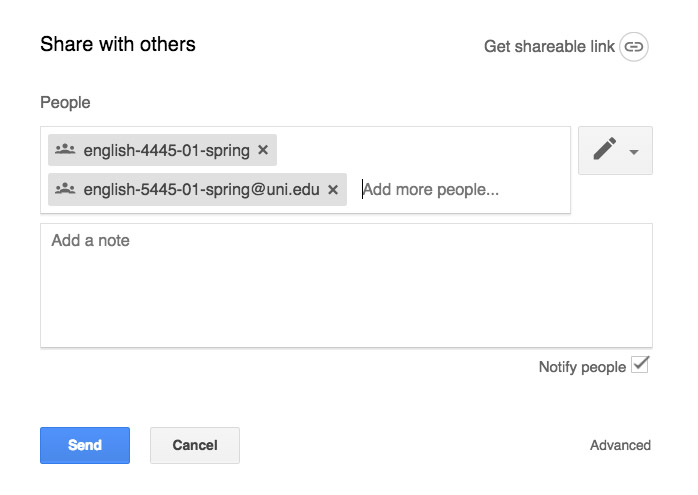
Once class begins, I share that file with the entire class (using the single Google Groups address each class has) and give the students writing privileges (that’s the pencil icon).
These class sessions then become bring-your-own-device days. However, I don’t need every student to have a laptop or tablet. Each group only needs to have one device, and with that, each group can simultaneously add their response to their specific slide.
There’s a bonus to this method. Though I will go around and check in with each group on their progress, it can often be difficult to perceive if a group is having trouble or is already done or if they’ve completely misunderstood the directions. However, the Google Slide file updates on the fly, and from the instructor computer I can watch all of the responses being written, allowing me to intercept in-process any emerging problems or snafus.

When the class comes together to have each group report back, I’m able to present the slides to the entire class, and after class, each group (and any student who missed class) will have access to that file. It is possible afterward, if for some reason I wanted to ensure that these slides were not altered, for me to change the permission setting for the class from “writing” to “viewing” (the eyeball icon).
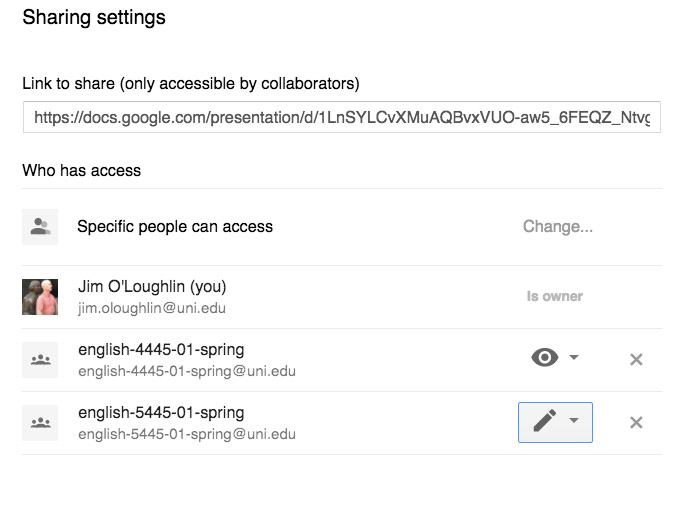
That would lock down the responses though the slides would still be available for reading. Of course, the whole slideshow could can also be embedded into a Google Site, if you want want to centralize these responses.
What I like about this class hack is that it does not represent a huge change in my pedagogy. It’s a simple use of readily-available technology, but it’s made group work more efficient and more practical.
Submitted by Dr. Melanie Abbas, Director IT-Educational Technology & Media Services, Computer Science Adjunct
I have been teaching CS 3730 Project Management for the past couple years and have been looking at ways to engage students in the classroom in the activities that support the content in what could be a very dry subject area. One area that is often hard to convey is the idea of project risk. This semester, I think I have finally found a way to use the technologies in the room to assist with this transfer of knowledge and also address the competency in the course of learning to use project management software.
By using the technologies in the StudioIT 1 (room ITTC 134), I was able to setup groups using one TV and a Solstice wireless display sharing device so that each group could collaborate on the decisions they were making. As an instructor, this also helps me to see that each group is working and walk around the room to discuss their decisions without hovering over a laptop or looking at a piece of paper on the table. I have used this same method any time I am having the students working on a group discussion. This keeps the note taking up on the TV for me to respond as I walk around the room. It also allows the rest of the class to see during our wrap up of the discussions
In regards to this particular activity, the class was put into teams who were given a project file using 30 day free trail of a project management software at gantter.com. Each group started with the same project file, a choice of staff and a fixed budget to update their file.They were given 20 minutes to set their project and prepare for the execution phase. During the execution phase, I drew random issues from a bag that would impact their project. For example, the ordered equipment was $1000 higher than estimated, a staff member was sick on a specific date, or a task took longer than expected causing delays. After several issues were drawn and schedules were adjusted, the team which completed their project the soonest with the lowest budget won (in this case, a bag of mini snickers!).
Students in the class mentioned that it helped them to have the group discussions on how to do the scheduling, use the software and think of possible issues that could go wrong. There is no way in a 5 week course that I could have students go through an entire project management cycle to learn about risk, but this activity could be done in one class period.
If you would like to know more about how I have used the room or schedule a tour of the room, please email me melanie.abbas@uni.edu
This classroom can be reserved for a specific class period activity, group meetings, or as the primary classroom for the entire semester (depending on availability).
If you are interested, please fill out a request for the space at: https://it.uni.edu/studio-it-or-computer-based-testing-center-reservation
January 28th is National Data Privacy Day, an educational initiative focusing on raising awareness among businesses and individuals about the importance of protecting the privacy of personal information. With more and more information being collected by companies, websites, and social media, this is something everyone should consider.
To understand the importance of Data Privacy day, it is vital to understand Personally Identifiable Information (PII) and exactly what privacy is. PII is any combination of data points that can lead to the identification of a specific individual (you). This can mean things such as your name or email address, but most times PII refers to “sensitive PII” such as Social Security, driver’s license, state identification, or financial account numbers. Sensitive PII can also exist if PII is combined with another piece of information about you such as a birthdate, medical information, or even passwords. The more pieces of data combined about an individual, the more valuable and sensitive the body of information becomes.
Privacy is often considered to be the concept of confidentiality, which is keeping information secret from those that should not see it. While that is an aspect of privacy, often called “need to know,” privacy is much more. Privacy is a larger concept centering on you as the individual to whom the information refers. It is about your rights to access, correct, and control the information that another entity has about you.
Privacy Rights:
Organizations that honor your privacy will not only protect confidentiality, but should follow a set of principles related to how they manage your information, including:
- Not collecting more information than they need to conduct their business with you;
- Informing you of what they will do with the information that they collect and not doing more with it than they have promised;
- Retaining the information for only as long as it is needed and then properly destroying the information;
- Not sharing your information with others without your permission, except as required by law;
- Allowing you to review and correct information if necessary.
To understand your privacy rights it is essential that you read the privacy policies of any organization to whom you provide information, especially PII. This includes websites, health care providers, insurance companies, and financial institutions. If you do not agree with how they intend to protect your privacy, consider not using their service.
Privacy is a Shared Responsibility:
While organizations and websites have a responsibility to protect your privacy, which most will outline in their privacy policy, this is also your responsibility. Social media users are especially susceptible to privacy concerns. Individuals voluntarily place enormous amounts of information about themselves, their friends, and associates, on social media. It is critical that everyone is aware of the information they post on social media services, such as Facebook, LinkedIn, Snapchat, and Twitter. This awareness is not limited to what you post about yourself, but what you post about others as well!
Identity Theft Protection:
Despite many organizations best efforts in handling and using your private information properly, the countless breaches of PII by cyber criminals in the past few years have resulted in the exposure of information about millions of people. One reaction to such breaches can be to provide credit monitoring for one year. This is a very short amount of time to have such a protection. Those that have stolen the information, or those to whom they have passed it on, may hold it for much longer than a year before using it to steal your identity, commit credit card fraud, or worse in your name. If you have been a victim of a breach, check out some of the FTC’s resources on starting a credit freeze to protect yourself.
If you are considering Identity Theft protection services, research the firms that you are considering engaging and ensure you understand the services they will and will not provide. Also, read their privacy policies, because for them to deliver these services you must provide them with varying amounts of PII.
Protecting privacy is both your responsibility and that of those individuals and organizations that have information about you. Do everything in your power to be aware of how you personally can compromise your privacy and hold those organizations that you engage with accountable for their management, or mismanagement, of your personal information.
For More Information:
US-CERT Data Privacy Day Events
Online Trust Alliance Data Privacy & Protection website
Stay Safe Online website: National Cyber Security Alliance
Forbes, Data Privacy Day: Easy Tips to Protect Your Privacy
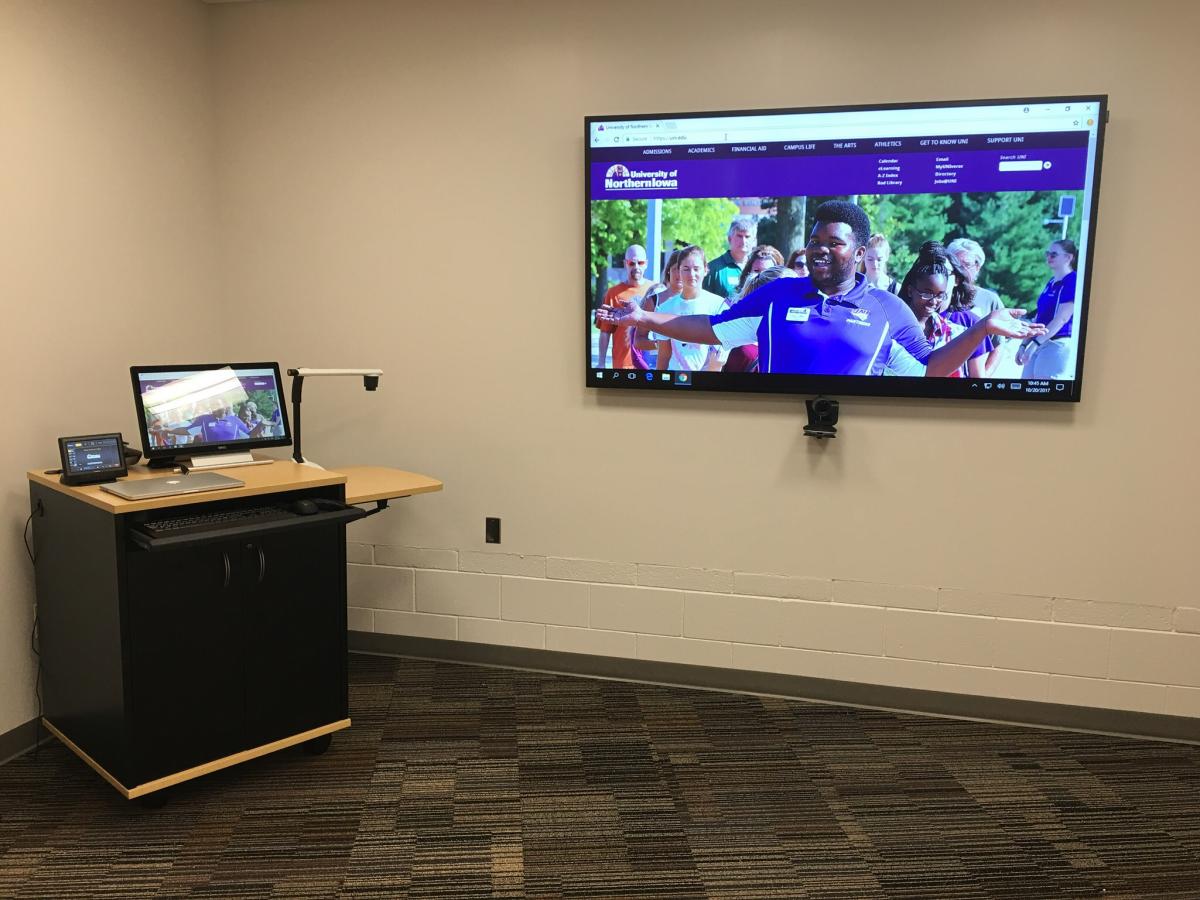
It is great to see another classroom / learning space installed and ready to use at the University of Northern Iowa.
Our team has the opportunity in assisting the campus with the technologies installed in various spaces. We provide services with assessing the technology needs for the space, acquisition, installation, and training for the technology within these spaces.
Training involves both the “what buttons to push” to make the classroom operate to “best practices” on how to utilize the classrooms to have the most effective impact for engaged student learning.
This classroom has the capabilities to support wireless or wired screen sharing from mobile devices, document camera, DVD player as well as high definition local and international video and audio conferencing capabilities. It also has an easy to use control system.
The room looks a little empty as the furniture has not been delivered. This room will have a table in the center. Several other rooms we have completed have movable tables and chairs to allow for active learning capabilities.
If you're interested, http://classrooms.uni.edu is our web page that has an overview of technologies installed in our base standard classrooms.
Off to the next adventure!

By the end of 2018 UNI will be requiring a higher level of security for your UNI email using a protocol called OAuth 2. If you use an application that doesn’t have this security today, it will not be able to connect the next time you change your CatID passphrase.
If you access your UNI email through a web browser (visiting uni.edu/email), no change is required and you will continue to access your email like you do today, but you will need to log back into your web browser.
If you use a mail application on your desktop or laptop, we recommend accessing your email through your web browser.
Do you use the Gmail app today or want to start using it? See our information on configuring your device using the Gmail app.
If you own an Apple device, you can also use the Gmail app.
Need further help or have additional questions? Experiencing an issue on or after the change? Submit an incident through Service Hub or contact the IT Service Desk at 319-273-5555.
Over the past two years, an initiative has been underway to upgrade the technologies within classrooms and learning spaces at the University Of Northern Iowa (UNI).
This initiative is focused on classroom and learning spaces in regards to upgrading aging technologies, providing a consistent experience, providing centralized support and training within these spaces. This initiative has been a collaborative effort involving Information Technology (IT), Students, Faculty, Staff, and Administrators.
A set of baseline technologies have been selected and are currently being integrated within classrooms and learning spaces across campus. The initiative is a multi-year initiative and will continue to be implemented in the future.
For more information about the project, technologies that are being installed, and contact information please check out the Learning Spaces web site at https://classrooms.uni.edu/


