Information Technology Updates
Citrix is a resource available to UNI students and faculty to access applications and desktops while off campus. Important changes to be aware of for Citrix at UNI are noted below.
Multi-factor Authentication
Citrix will start requiring MFA via Duo on August 10th, 2021 to match campus security standards. If you currently use Duo, you will start to see this change on August 10th. If you are a student that currently does not have Duo turned on, you won’t be prompted by Duo to access Citrix until it is turned on for your account. When this option is available, you will receive communication from campus IT. If you would like to learn more about multi-factor authentication at UNI, visit this page https://mfa.uni.edu.
New Interface
Citrix is now available via your web browser! Simply navigate to https://vdi.uni.edu and access the applications and\or desktops in your web browser without having to download a client. You can continue to use the client, but we encourage you to give the web client a try.
If you decide to continue to use the client, no problem! When using the Citrix client you will not receive a prompt asking your preference for your Duo authentication. You can expect this Duo prompt to come to your phone and are required to verify your identity before you can log into the client.
Google has notified UNI IT they will be applying a Drive Security update to make link-sharing more secure on September 13, 2021. Security is a critical factor in managing our data in Google Drive, so we will be applying this update to a some of the files in our domain. Google will be sending an email on July 26th (similar to the message below) to users with impacted files, this will includes actions you will need to take and a link to the impacted files.
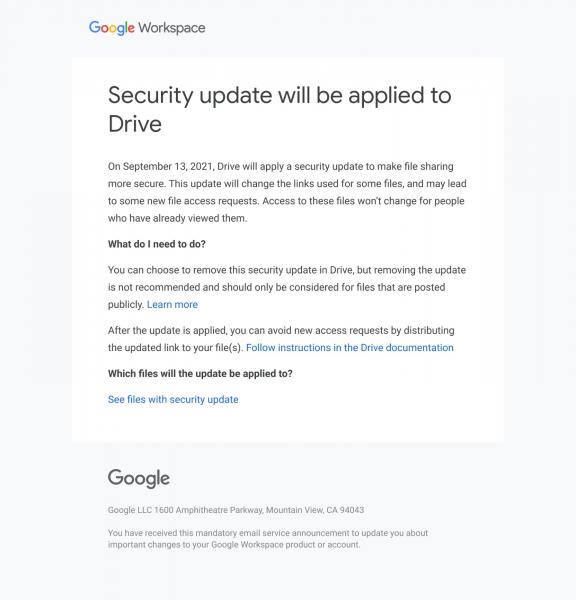
Here are some important aspects we have learned about this change:
- Files that will be affected by this security update are non-native Google files (e.g. Microsoft Word, PDFs, MP4s, etc.) shared prior to 2017. Google files (Docs, Sheets, Slides, and Forms) will not be impacted.
- Any Google user (internal or external) should be able to access any file they have accessed before, even after the update has applied. Users can request access if they have not accessed the file before the update.
- Only users (internal or external) who haven’t viewed the affected files previously will be affected by this change. If a new user uses the old link, a request will be sent to the data owner to allow access.
- You will need to share a new updated link (URL) for any files that still need to be publicly accessible with a link on websites or posted elsewhere. New links can be generated starting July 26th.
We ask that if you have questions or concerns about this email, please contact UNI Information Technology via servicehub.uni.edu and your question or concern will be routed to the appropriate team.
Additional information from Google can be found at: https://workspaceupdates.googleblog.com/2021/06/drive-file-link-updates.html
I wrote about ransomware about a year ago. The only things that have changed since then are that the result of becoming infected have gotten far more severe and the number of victims has increased exponentially. Today's variants not only encrypt your data and demand payment to decrypt it, they also steal your data and threaten to expose it to the world if payment is not made. Under that scheme, even if you have proper and sufficient backups to restore your data, making the encryption moot, there is the threat that your data will be published for all to see.
We are not immune from these attacks here in the midwest. Last fall, the University of Nebraska Medical Center and Nebraska Medicine were breached. Associated costs are many tens of millions of dollars. More recently, and even closer to home, DMACC suffered a ransomware attack early last month that shut their network and classes down for almost two weeks.
Phishing provided the initial foothold for the bad actors behind these and many other similar incidents. Vigilance and skepticism when reading email remains key. Don't fall for the emotions that all phishing actors try to evoke -
- Fear - something bad will happen if you don't click on the link in the message
- Greed - something good will happen if you do click on the link in the message
- Urgency - hurry up and click on the link in the message right now
- Concern/Empathy -
- I’m stranded in an unfamiliar city
- I’m falsely accused, in jail, and need bail money
- I’ve been mugged and am in the hospital
Don't click on links in email messages unless you're certain they are legitimate. Don't open attachments in email messages unless you're certain of the sender's identity and the content of the message makes sense to you. If you have any questions about the message, err on the side of safety and seek help by contacting security@uni.edu.
Mobile devices are an amazing and easy way to communicate with friends, shop or bank online, watch movies, play games, and perform a myriad of other activities. Since these devices are such an important part of your life, it is essential to keep you and your devices safe and secure. Read more at https://www.sans.org/newsletters/ouch/securing-mobile-devices/
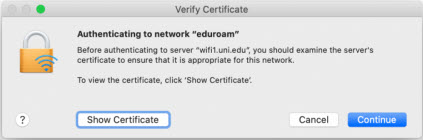
On June 18th Information Technology will replace the security certificate used to secure connections to Eduroam WiFi on campus. All UNI-owned and managed devices will be automatically reconfigured for the new connection and nothing will be required. However, personally owned laptops, tablets, and smart phones will potentially be asked to accept a new security certificate the first time they connect to Eduroam WiFi on June 17th. These prompts could look something like the screen captures below.
If you have questions or trouble connecting to Eduroam WiFi on campus, please visit this IT support article. You can also contact your IT support by submitting a "Get IT Help" request from the Service Hub Portal.
Windows 10
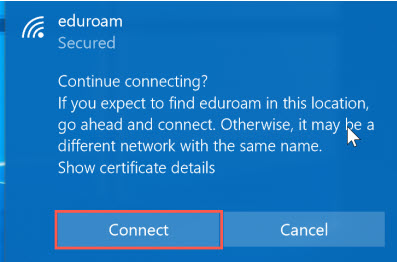
iOS
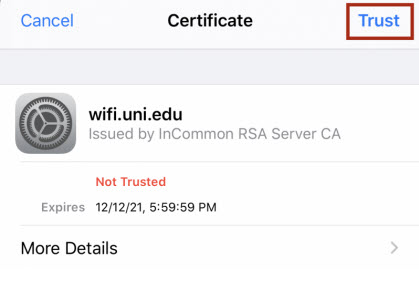
MacOS
Mobile devices, such as tablets, smartphones, and smartwatches, have become one of the primary technologies we use in both our personal and professional lives. What makes these devices so powerful are the thousands of apps we can choose from. These apps enable us to be more productive, communicate and share with others, train and educate, or just have more fun. Here are steps you can take to securely use and make the most of today’s mobile apps. Read them at https://www.sans.org/newsletters/ouch/securely-using-mobile-apps/
Vishing is to your phone as phishing is to your email account. Vishers may use either voice or SMS (text messages) to target you. They do this because there is less protection for your phone than for your UNI email account. Read the SANS OUCH! page at https://www.sans.org/newsletters/ouch/vishing/ for details and advice.

In an announcement earlier this calendar year, Google notified their education customers that they are changing the rules regarding storage for their Google Workspace for Education product line to no longer include unlimited storage space. Although Google has traditionally offered unlimited storage for free to its education customers, this model has become unsustainable with the rapid acceleration in growth of stored data. In July of 2022, Google will shift from unlimited storage to a pooled storage model for Google Workspace for Education customers.
This shift in strategy by Google means that UNI will need to reduce it’s overall storage consumption across Gmail, Google Drive (both My Drive and Shared Drives), and Google Photos in the Uni.edu Google domain prior to the July 2022 deadline. Information Technology (IT) is working closely with Google to ensure we have the tools and resources necessary to help us make this transition as smooth as possible.
IT will be communicating soon with users across campus who are using significantly more storage as compared to the average in our domain to understand their needs and work with them to clean up old and unneeded files and data. IT will continue to share information and answer questions as this project progresses. In the meantime, if you’re interested in seeing how much storage you’re using with your UNI Google account, or to find out how to reduce your overall storage usage, you can review this knowledge base article.
A W2 tax email scam is circulating in the U.S. using Typeform, a popular software that specializes in online surveys and form building. The campaign is aimed at harvesting victims’ email account credentials, researchers said.
According to Armorblox, the campaign also bypasses native Google Workspace email security filters in the victims it examined.
“The email impersonated an automated file-sharing communication from OneDrive, informing victims that they had received a file,” researchers explained in an analysis on Tuesday. “The email was sent from a Hotmail ID and was titled ‘RE: Home Loan,’ followed by a reference number and the date, making it seem like the email was part of an ongoing conversation to lend it more legitimacy.”
To read the complete article see:
https://threatpost.com/tax-phish-google-workspace-email-security/165376/
See also:
https://www.armorblox.com/blog/blox-tales-w2-tax-scam-using-typeform/
The [US] Internal Revenue Service (IRS) is warning of ongoing phishing attacks impersonating the IRS and targeting educational institutions. The attacks use tax refund payment baits and mainly focus on universities' staff and students with .edu email addresses.
- The rest of the story: https://www.bleepingcomputer.com/news/security/scammers-target-universities-in-ongoing-irs-phishing-attacks/
- IRS warning: https://www.irs.gov/newsroom/irs-warns-university-students-and-staff-of-impersonation-email-scam
- Researcher's blog: https://abnormalsecurity.com/blog/irs-impersonation/


