Visitors Updates
Phishing attacks have become the most common method cyber attackers use to target people at work and at home. Read more at https://www.sans.org/newsletters/ouch/phishing-attacks-getting-trickier/
Should you use a different password for every site? Absolutely! Should you use your browser to store all of those distinct passwords? Probably not..
https://isc.sans.edu/forums/diary/Use+Your+Browser+Internal+Password+Vault+or+Not/28658/
While social media is a fantastic way to communicate, share, and have fun with others, it is also a low-cost way for cyber criminals to trick and take advantage of millions of people. Don't fall victim to the three most common scams on social media. Read more at https://www.sans.org/newsletters/ouch/top-three-social-media-scams/
I have recently attended several briefings on the cybersecurity fallout from the current Russia-Ukraine conflict in eastern Europe. That event has resulted in a lot of FUD (Fear, Uncertainty, Doubt) about the online safety of people worldwide. It is certainly true that cyberattacks have played a role in the conflict, but cyberattacks are present every day. There are three general areas that you can concentrate on to protect yourself and your cyber assets.
- Phishing - Be aware and be skeptical of email you receive, particularly from unknown senders. The bad actors will try to fool you by using well-known personal names on the accounts they are using. They may also copy signature blocks, UNI logos, and other details to make their message appear official. Check the actual email address of the sender. Hover over links with your mouse to see where they are going. If it's not uni.edu or another well-known site, think again and don't click the link.
- Passwords - Passwords are hard and not really sufficient on their own today. They should be unique from one site to another and should be more than a simple word or two. Length trumps complexity. Even though "thequickbrownfoxjumpedoverthelazydog" has several issues and shouldn't be used, it is far better than "R3(s4*#1" for a password. Consider a password manager to help. It can generate lengthy unique random passwords per site and remember them for you.
- Patching - For UNI-managed devices, IT tries to take care of this for you but the process does take your cooperation and time to allow the patches to be deployed and made active. For your personal devices, patching is on you. Allow the operating system and applications to apply updates automatically. And when Windows or Adobe or Office tells you their are patches available, let those updates happen. If you can't do that immediately, okay, but do it soon, within a day or two.
Physical objects as security threats are in the news at the moment. The oft-touched upon tale of rogue USB sticks is a common one. Being wary of random devices found on the floor, or handed out at events is a smart move. and now they're showing up in the mail. You simply don’t know what’s lurking, and it’s hard to find out safely without the right tools available. Even then, something can slip by and cause no end of trouble on your desktop or network. Read more at https://blog.malwarebytes.com/cybercrime/2022/01/attackers-are-mailing-usb-sticks-to-drop-ransomware-on-victims-computers/
US Police Warn of Parking Meters with Phishing QR Codes
Always think twice when you're tempted to scan a QR code!
https://www.bitdefender.com/blog/hotforsecurity/us-police-parking-meters-phishing-qr-codes/
The holiday season is nearing. Soon millions of people will be looking to buy the perfect gifts, and many of us will shop online. Unfortunately, cyber criminals will be active as well, creating fake shopping websites and other online shopping scams to steal your information or money. Learn how you can find good deals without becoming a victim at https://www.sans.org/newsletters/ouch/shopping-online-securely-nov-21/
I wrote about ransomware about a year ago. The only things that have changed since then are that the result of becoming infected have gotten far more severe and the number of victims has increased exponentially. Today's variants not only encrypt your data and demand payment to decrypt it, they also steal your data and threaten to expose it to the world if payment is not made. Under that scheme, even if you have proper and sufficient backups to restore your data, making the encryption moot, there is the threat that your data will be published for all to see.
We are not immune from these attacks here in the midwest. Last fall, the University of Nebraska Medical Center and Nebraska Medicine were breached. Associated costs are many tens of millions of dollars. More recently, and even closer to home, DMACC suffered a ransomware attack early last month that shut their network and classes down for almost two weeks.
Phishing provided the initial foothold for the bad actors behind these and many other similar incidents. Vigilance and skepticism when reading email remains key. Don't fall for the emotions that all phishing actors try to evoke -
- Fear - something bad will happen if you don't click on the link in the message
- Greed - something good will happen if you do click on the link in the message
- Urgency - hurry up and click on the link in the message right now
- Concern/Empathy -
- I’m stranded in an unfamiliar city
- I’m falsely accused, in jail, and need bail money
- I’ve been mugged and am in the hospital
Don't click on links in email messages unless you're certain they are legitimate. Don't open attachments in email messages unless you're certain of the sender's identity and the content of the message makes sense to you. If you have any questions about the message, err on the side of safety and seek help by contacting security@uni.edu.
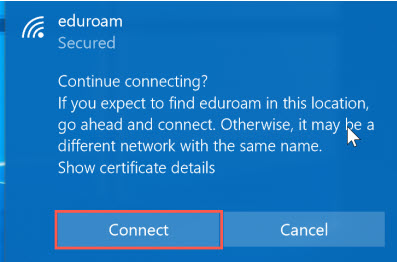
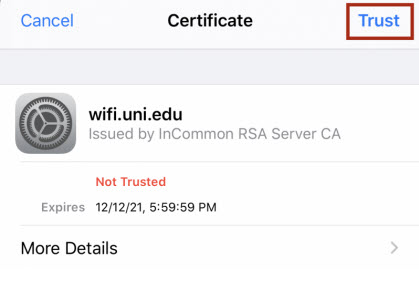
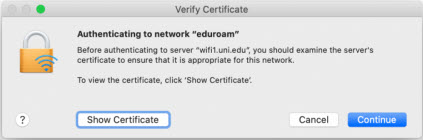
On June 18th Information Technology will replace the security certificate used to secure connections to Eduroam WiFi on campus. All UNI-owned and managed devices will be automatically reconfigured for the new connection and nothing will be required. However, personally owned laptops, tablets, and smart phones will potentially be asked to accept a new security certificate the first time they connect to Eduroam WiFi on June 17th. These prompts could look something like the screen captures below.
If you have questions or trouble connecting to Eduroam WiFi on campus, please visit this IT support article. You can also contact your IT support by submitting a "Get IT Help" request from the Service Hub Portal.
Windows 10
iOS
MacOS
Mobile devices, such as tablets, smartphones, and smartwatches, have become one of the primary technologies we use in both our personal and professional lives. What makes these devices so powerful are the thousands of apps we can choose from. These apps enable us to be more productive, communicate and share with others, train and educate, or just have more fun. Here are steps you can take to securely use and make the most of today’s mobile apps. Read them at https://www.sans.org/newsletters/ouch/securely-using-mobile-apps/


